You have spent hours making the content of your website truly unique and probably have a monetization concept that includes individual accounts for your clients.
If that is the case you most likely want to avoid account abuse and avoid multiple logins at the same time into your WordPress. Luckily Session Manager has you covered.
One advanced feature of the Session manager is the possibility to allow the login to the dashboard even if the session limit is reached. This way the user experience stays great. Your clients cannot access the protected content while their session limit is exploited.
To enable an easy way to self-manage the sessions, we have implemented a nice ajax table. Use the shortcode [session-list] to display a responsive table that shows all current sessions.
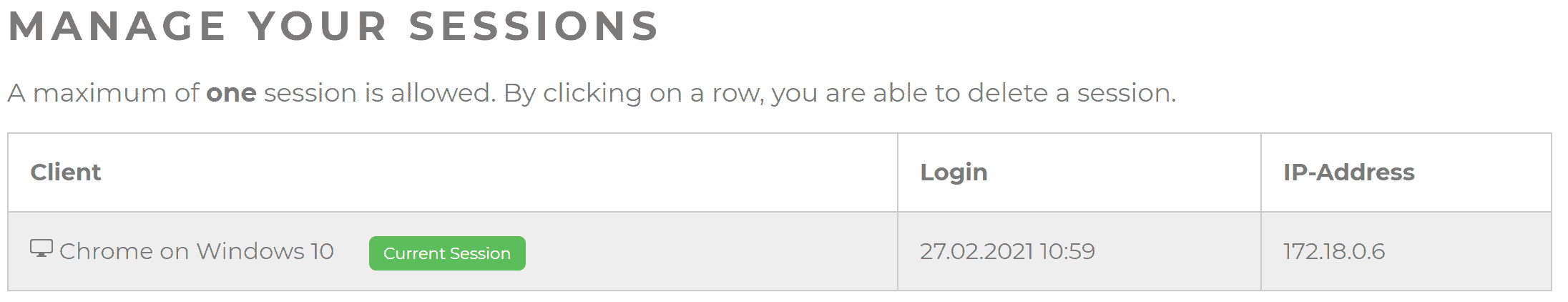
With a simple click on a row, the user can destroy one of the sessions. A badge show if the user is trying to destroy his current sessions. If this happens a new login is required.
Session Manager has included various filters and actions to enable an easy way to customize the logic behind it. Let's take a look at the following code snippet:
add_action("template_redirect", function() {
// Array with post IDs
$posts_to_block = array(1,2);
// Check if current posts is one to protect
if (!in_array(get_the_ID(), $posts_to_block) ) {
return;
}
$within_limit = apply_filters("is_within_session_limit", true, wp_get_current_user());
if (!$within_limit) {
// If referrer could be determinde redirect there else home url
$url = wp_get_referer() === false ? home_url() : wp_get_referer();
wp_safe_redirect($url);
exit;
}
});This tiny piece of code checks on every redirect if the current post has one of the ids in the $posts_to_block array. If so the user is getting redirected to the referring URL, or if it could not be determined to the home URL.
This snippet is ready to go and can be copy and pasted in your functions.php . It is easily customizable to check for post types, users, user roles, or anything else you can imagine.
The Session Manager Plugin allows you to completely lock users out if they have reached the session limit. This feature is easier to use than the method we discussed before.
Simply active the integration in your WordPress backend under Users -> Sessions -> Integrations and activate "Block users from logging in if the session limit is reached".
At this point, logins for users that already have reached a maximum amount of parallel logins are prohibited. A notification mail with a link to destroy all existing sessions will be sent to the user's mail address. A simple click on that mail will unlock the account.
The mail will also include a table with the last existing 5 sessions.
Blocking the login is a good thing to protect your contents. Sending the user an email ensures, that the "real" owner knows what's happening with their accounts. Also, it stops abuse because the owner will likely become annoyed by always destroying the existing user sessions.
But this can also impact the user experience. The user only knows that the session limit is exceeded after he successfully logged in. When he destroys the sessions with a click on the link in the notification mail, he needs to enter his credentials again.
To avoid this our Session Manager has an autologin option. When activated, the user will not only destroy all existing sessions but also be logged in with a new fresh session. This avoids re-entering the credentials.
